Connectivity required between On-Premises Datacenter, VMware Cloud on AWS SDDC, Internet, and Amazon VPC.
There are two type of networks in Cloud SDDC defined for control and security purpose.
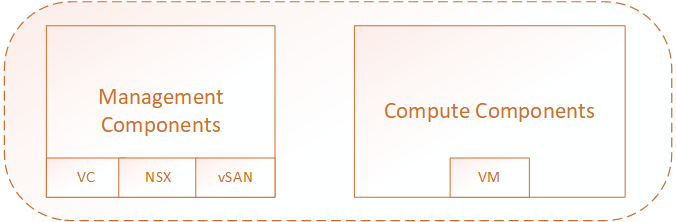
These parts carry different components of a Cloud SDDC environment, as listed below. Management Gateway (MGW) provides connectivity to vCenter and NSX devices, whereas Compute gateway (CGW) provides connectivity to actual workload which is in form of Virtual Machines.
|
Type |
Components |
Accessed Via |
|
Management Components |
vCenter, NSX, vSAN |
Management Gateway (MGW) |
|
Compute Components |
Virtual Machines |
Compute Gateway (CGW) |
Management Gateway (MGW) utilizes NSX Edge Security gateway to provide the connectivity to management Components, and Compute Gateway (CGW) utilizes NSX Edge and DLR to provide the connectivity to Compute Components.
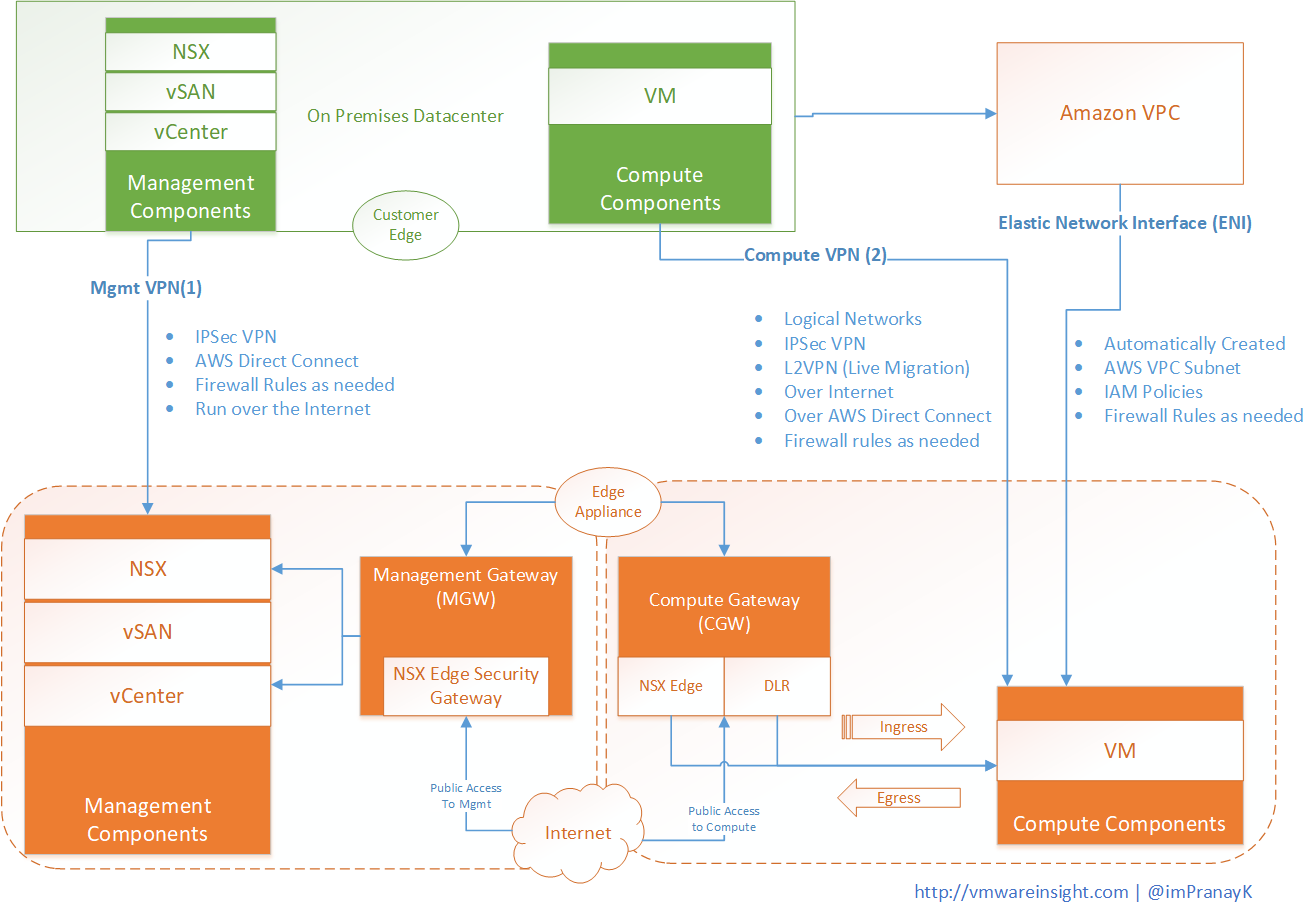
While preparing for VMware Cloud on AWS, we need to understand the network framework of Vmware Cloud on AWS SDDC environment, and need to understand how it provides connectivity between your On-Premises datacenter, your VPC, and Internet. below are the components which must be communicate with each other in order to work provide functionality.
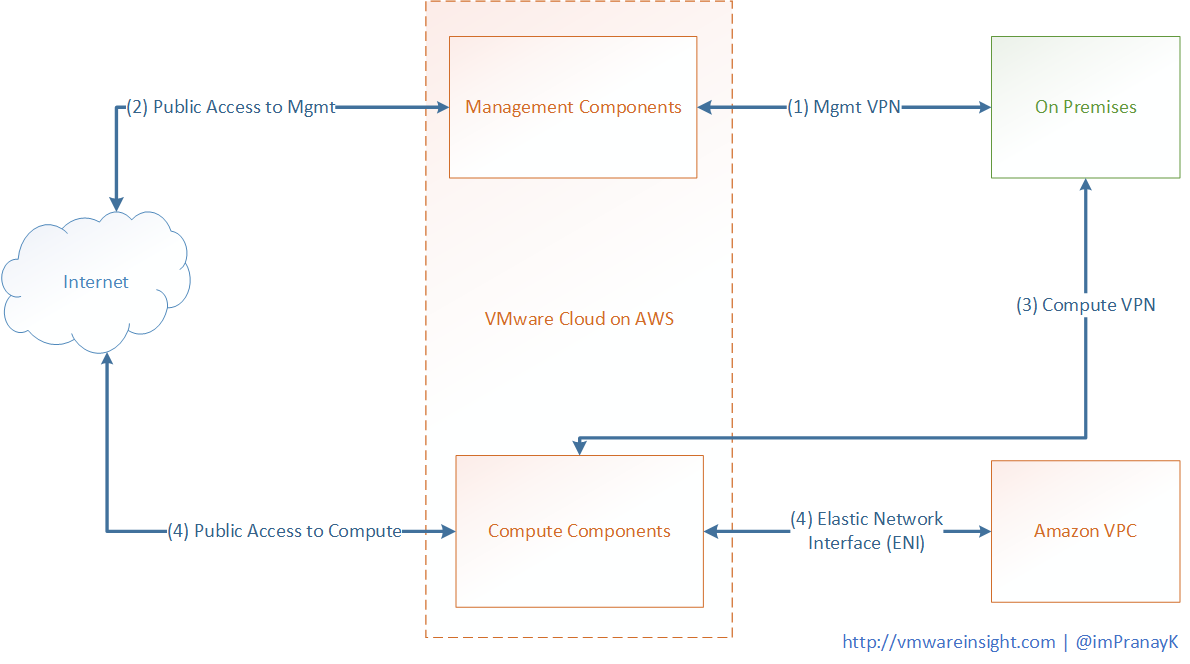
You need to create a management VPN and determine the range of IP address that will be used by this management components. This address range will be in form of CIDR block. Once Cloud SDDC is provisioned, you need build an IPSec VPN which will be between your on-premises datacenter and management components. This VPN travels over the internet or over AWS direct connect. Once connected, you can create firewall rules in the VMware Cloud on AWS console to control access to the vCenter Server for your on-premises datacenter.
The next connection is optional, it is only needed if you need your vCenter access over the internet. A public IP for your management components will automatically be provided during the provisioning process. However, all access to this IP is restricted. To provide internet connection, you need to create firewall rules in VMware Cloud on AWS console to allow the direct type of internet access.
Second VPN you need to create is Compute VPN between Compute Components and On-Premises Datacenter. To do this, we will need to create several logical networks that will provide the IP address to the Virtual machines that you migrated or build in VMware Cloud on AWS. This VPN allow VMware Cloud on AWS workloads to communicate with On Premises workloads. Vmware Cloud on AWS allows customers to leverage IPSec Layer 3 VPNs as well as Layer 2 VPNs. It enables you to stretch on-premises data link layer (Layer 2) to the Cloud SDDC environment. L2VPN uses for live migration. It works over the internet or over the AWS direct connect. To secure the environment, we create firewall as needed.
Next connection is between Cloud SDDC Virtual machines (Compute Components) to Amazon VPC in form of Elastic Network Interface. It automatically created during SDDC provisioning process. Once you select AWS VPN associated through your Cloud SDDC, elastic interfaces will be created, which will allow traffic to flow between the Cloud SDDC Compute environment. To control the security, you create IAM policies on AWS site, and firewall rules on VMware Cloud on AWS.
Finally, you want to get access to some of your Compute workloads of Cloud SDDC. You need internet access to access over public. You need to leverage AWS elastic IPs along with NAT and firewall rules to allow the public access to the workloads. This can be done from Networking interface of Vmware Cloud on AWS Console
There are certain discussion points which need to make while planning to deploy your Cloud SDDC, as listed below.
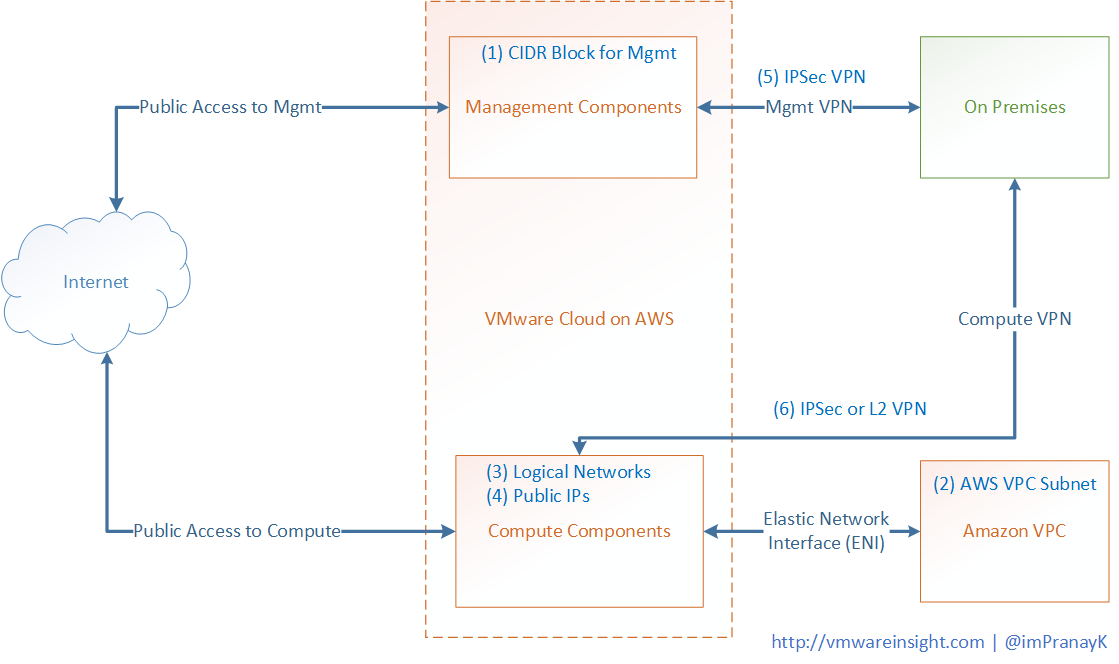
First information we required is CIDR Block for Management components. It provides IPs to the SDDC domain which are managed by VMware, like ESXi Host and vCenter Server. Maximum number of hosts in SDDC depends on the network mask.
|
Mask |
Max # of Host |
|
/23 |
13 |
|
/20 |
125 (Recommended) |
|
/16 |
2045 |
Dedicated subnet in Amazon AWS VPC to connect VMware cloud on AWS. This information will again be used during deployment process and will be used unique elastic interfaces connectivity.